Why do attackers constantly target smartphones?
Approximately 83.72% of the world's population owns a smartphone. Their popularity, as well as the amount of data people store on their smartphones, naturally attracts attackers. Smartphones are no longer just for making calls or sending messages. They contain a huge amount of sensitive data that is extremely valuable to attackers. What might interest an attacker, when gaining access to your device? Here are a few areas:
- Communication: An attacker can monitor your SMS, emails, chat apps (e.g. WhatsApp, Messenger) or even eavesdrop on your calls. The obtained data can be used for blackmail or phishing attacks.
- Photography and video: Personal or sensitive files can be stolen, misused for fraud, creating a false identity, or used for blackmail.
- Financial data : Access to banking apps, payment cards, and mobile wallets can lead to unauthorized transactions and theft of money.
- Location data : GPS on your smartphone allows an attacker to track your movements in real time, which can lead to physical tracking or theft.
- Digital keys and documents: If your phone contains an electronic ID card, insurance card, or digital keys to a car or building, an attacker can gain access to your identity and assets.
- Microphone and camera: A compromised device can be used to secretly record audio or video without your knowledge.
- Personal documents and access data : Saved passwords, contacts, or important files can be misused for further attacks or sold on the dark web.

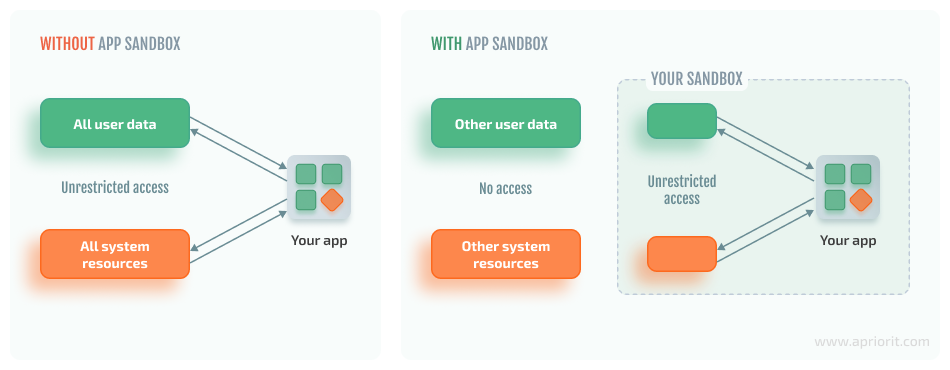
Isolated application environment
When talking about attacks on applications, it is important to know that most modern applications run by default in a so-called "sandbox". This is an isolated environment, where applications operate with limited permissions. This means that applications do not have access to all parts of the device and its data. If they need to work with another part in order to function, the user must grant them permission.
A permission allows access to certain functions or data on the device. Most often, an application requests it when it first starts. It is important not to give unnecessary permissions to applications that do not need it (e.g., a calculator does not need access to our contacts). Some applications can abuse user permissions. The goal of attackers is to manipulate the user into granting the requested permissions.
How can an attacker abuse privileges?
Logging in to banking, email, and other services often requires a verification code via SMS (second factor). Attackers can abuse access to SMS and steal these codes, gaining access to sensitive data even when two-factor authentication is in place.
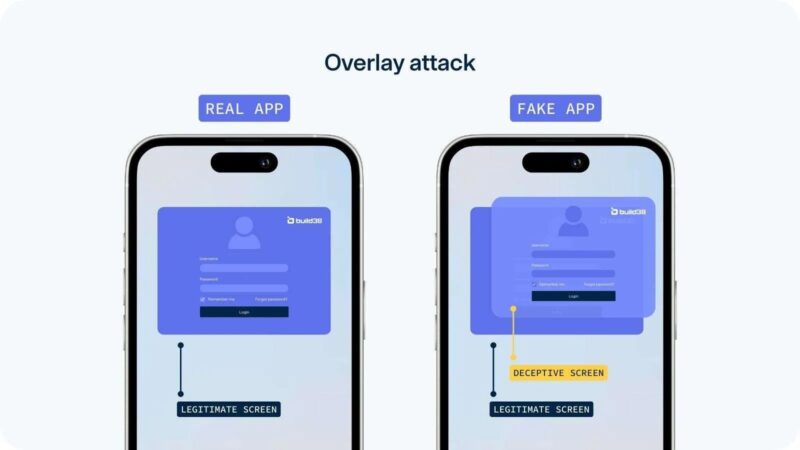
These services allow screen overlays and alternative text input, especially for people with visual impairments. Since they require special permissions to overlay the screen, they can be abused by attackers to capture everything you do. The image shows how a fake window overlays the real application. The user unknowingly enters their data into a fake form, which sends it to the attacker.
Not all malware requires user approval. Sometimes, opening a malicious website or receiving a text message is enough. These are cases where attackers bypass the granting of permissions by exploiting logical errors (security vulnerabilities) in the code. The process of exploiting a vulnerability is called exploitation.
Mobile phone exploitation
Exploiting phones is typically extremely complex and requires exploiting multiple vulnerabilities simultaneously. Below is an example of an exploit using Pegasus spyware.
Step 1: The user receives an SMS or message via the app, for example: “You have a new voicemail. Click this link to listen” or a threatening message.
Step 2: The user clicks on the provided link, which redirects them to an infected website.
Step 3: Without the user's knowledge, Pegasus spyware is installed on the device, which exploits operating system vulnerabilities (unknown to the developers).
Step 4: The attacker can now access messages, emails, and contacts, activate the microphone and camera for surveillance, track the device's location, and more. The attacker will obtain sensitive information that can be used for extortion, surveillance, or other malicious activities.