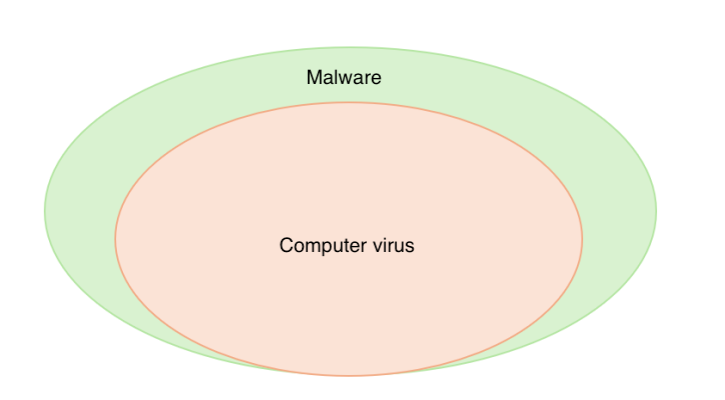
Malware is a broad term that includes various types (forms). We can distinguish individual types based on their attributes or properties. This is an approximate classification that is constantly changing and being supplemented. Based on an estimate of the type of malware, the user will be able to determine steps to prevent its consequences, or determine the damage.
Malware is most often confused with the term virus, which is just one type of malware.
Types of malware
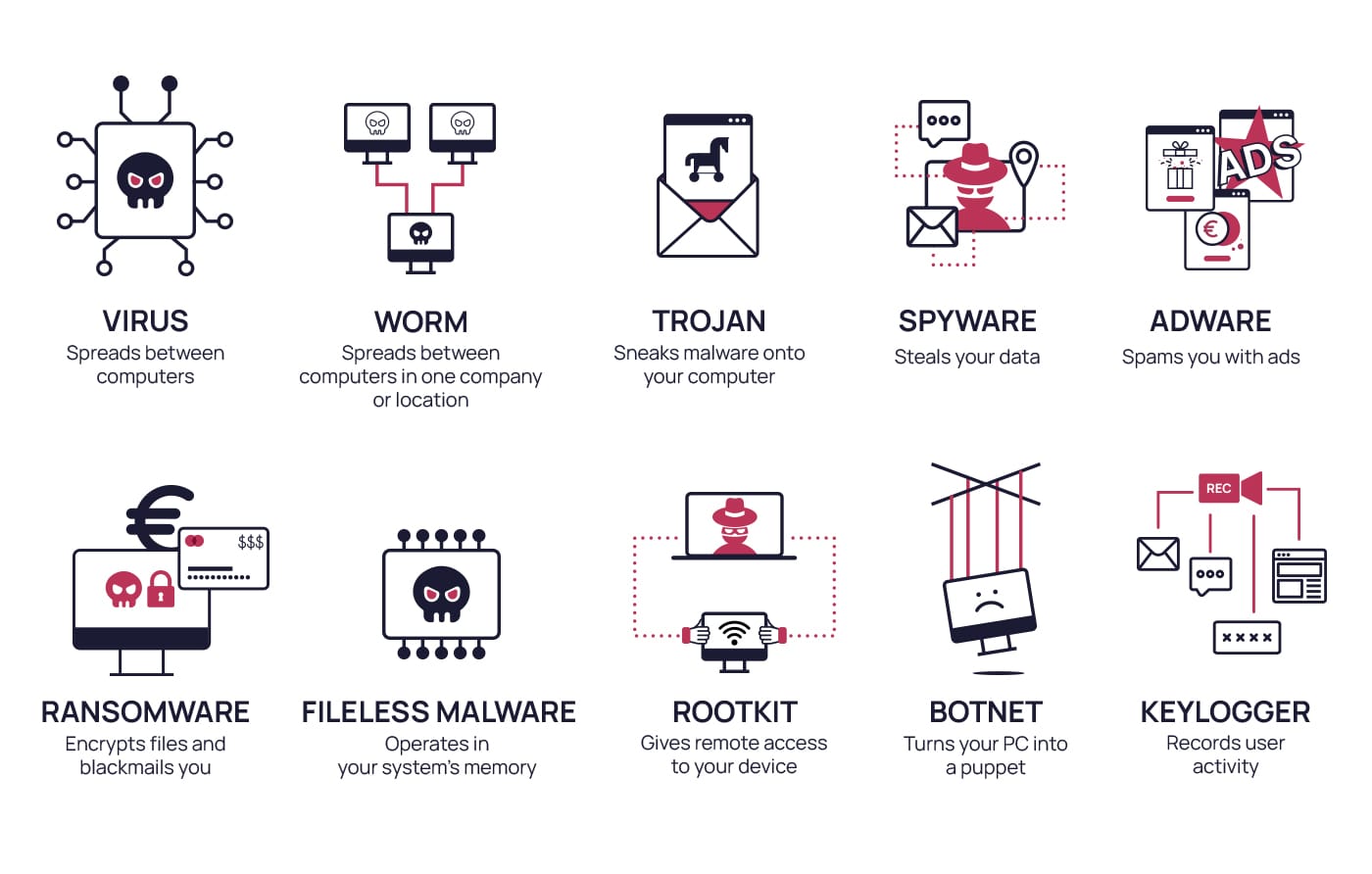
Viruses often spread to other computers by attaching themselves to various programs and executing code when a user runs one of these infected programs.
A virus spreads from system to system by attaching its code to other files. Once the file is accessed, the virus activates and performs whatever attack or action the attacker wants.
Viruses can also spread through scripts, documents, and vulnerabilities in web applications.
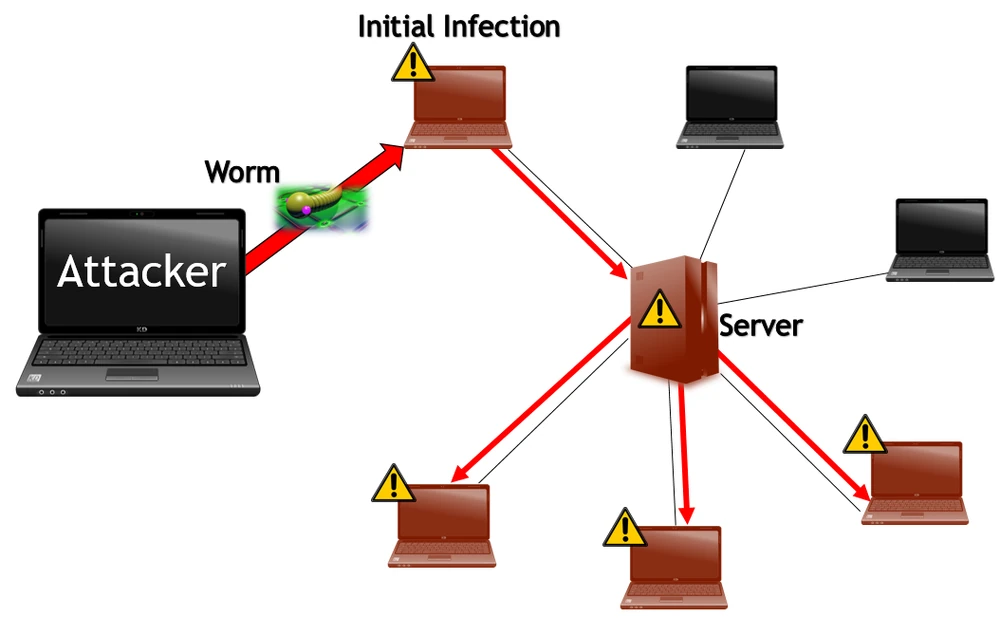
They spread across computer networks by exploiting vulnerabilities in operating systems.
Worms typically cause damage to computer networks by overloading those networks or overloading web servers.
Computer worms differ from viruses in that they have the ability to replicate and spread independently, while viruses rely on human activity to spread.
This malware restricts a user's access to the computer by either encrypting files on the hard drive or locking the system and displaying ransom messages.
This is how attackers try to force the user to pay a ransom, which is often in Bitcoin or another digital currency. Once paid, the restrictions are removed, and the user is given full access to their device or data.
In practice, it often happens that after paying a certain amount of money, attackers demand a higher amount of money, or the program to decrypt files does not work or is not provided.
Ransomware usually spreads itself as a computer worm that gets onto a device through a downloaded file or other vulnerability in the operating system or application.
After a ransomware attack, data often cannot be restored (decrypted), so we recommend backing up your data to external or cloud storage.

Named after the horse used by the Greeks as a ruse in the Trojan War, a Trojan horse disguises itself as a regular program but allows others to remotely access an infected computer.
Once an attacker has access to an infected computer, it is possible for the attacker to steal data (login details, personal information, even electronic money), install more malicious programs, modify files, or monitor user activity.
Trojans usually appear as audio or video plug-ins, required to play a music or video file, watch online videos, web browser plug-ins, games, or something fun or useful.
It is a type of malware that automatically displays advertisements, such as pop-up ads on websites or in applications, and can be included in free applications bundled with ads to generate revenue.
Adware can also be associated with spyware, which tracks user activity and collects information.

It is a type of malware that silently tracks and collects user activity, including keystrokes and sensitive data, and often changes the security settings of browsers and applications.
Its spread often exploits program vulnerabilities in conjunction with Trojan horses or even legitimate programs.

It is a type of malware that automates various specific operations.
The attacker takes control of the device using malware. The attacker tries to keep the user unaware that the bot is on their device.
Although some are intended for benign purposes such as video games, online auctions or competitions, malicious use, for example in botnets (a group of computers controlled by third parties) used for DDoS (overloading applications, websites or services, leading to their inoperability) attacks or spamming (sending unsolicited email) is more and more common.

It is designed to remotely access or control a computer without being detected by users.
It constantly hides its presence, so typical security products are not effective in detecting and removing rootkits.
Rootkits allow attackers to hide malicious processes, files, and the like, ensuring long-term control over the infected system.
They are detected by special rootkit scans.
It is a special type of malware that can silently monitor and record all keystrokes and activities performed on a user's device.
It captures data such as:
- login names
- passwords
- credit card numbers and bank details
- private message content
- other sensitive data.

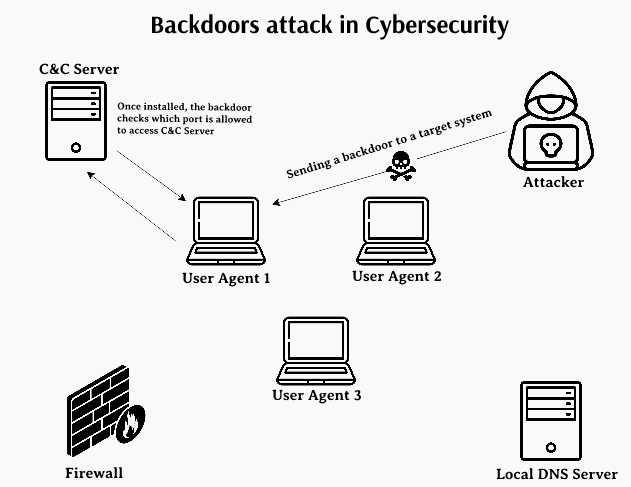
It allows remote access to an infected computer and control of that computer without the user's knowledge.
A backdoor bypasses common security mechanisms such as passwords or firewalls, allowing attackers to perform various malicious activities, such as:
- Installing additional malware (ransomware, keyloggers, spyware)
- Obtaining sensitive data (passwords, files, financial information)
- Using the computer for other attacks (e.g. DDoS attacks)
- Creating botnets – a network of infected devices controlled by an attacker
Malware targets
An important characteristic of malware is the goal the attacker is after. A quick overview of the goals of malware authors gives a good idea of why the malware threat is so serious:
- Credit card or other banking information: Credit card information and related personal information are a tempting and common target. Once this information is obtained, an attacker can purchase any type of product or service (e.g., web services, games, merchandise, or other products).
- Passwords: They are a very attractive target for attackers. Compromise of this type of information can be devastating for victims. Most users use the same passwords for several or all systems, including sensitive ones (e.g. internet banking, email account).
- Confidential or insider information: An attacker can use malware to effectively obtain such information from an organization to gain competitive or financial advantage.
- Storing malicious or illegal content: In some cases, a system infected with malware can be used to store data without the owners' knowledge. Uploading data to an infected system can turn that system into a server that shares any type of content (e.g., movies, pirated software, pornography, malware, financial data, or even child pornography).